Automatic SSL Certificates for internal IP's for home microk8s setup using LetsEncrypt

One of the issues I discovered while playing with microk8s Kubernetes setup locally was that many services and tools like Kubernetes Dashboard uses HTTPS for access and I don't want to use Self-Signed SSL certificates as it would require me installing these certificates in every device I use which would be a pain in the butt. So I was on the journey finding a way to have an SSL Certificate for my internal IP addresses. This article will document my journey of getting automatic SSL certificates for my internal microk8s Kubernetes setup.
SSL Certificate for internal IP address?
My first question was is there a way to get an SSL certificate from Public trusted Certificate Authority after looking at many free services like Let's Encrypt and similar services don't provide certificates to IP addresses, but only to domain names.
After discovering the issue with no way to get an SSL certificate for internal IP I was looking into other options for my problem. After racking my brains for a few minutes I had a question: Could I create a DNS A record for internal IP and would it work? A quick visit to my DNS control panel adding A record to the local IP address and visiting the domain name and seeing my local IP address served website I was amazed that it worked.

Discovering that I can have a domain name for internal IP working I was surprised now I had curiosity if I will be able to use service like Let's Encrypt to generate an SSL Certificate for this domain name but if I remember correctly the Let's Encrypt requires external access to verify domain name ownership. Hmm, maybe there is a way to verify domain name ownership without external access? After some digging around Let's Encrypt documentation, I found that there many ways to verify domain ownership one of them is DNS plugins which have many DNS providers to automatically verify domains by modifying DNS records using API from those providers. In my case it is DigitalOcean.
Following certbot-dns-digitalocean documentationI tried to generate a certificate for internal IP but I ran into the issue that default macOS certbot installation from brew install certbot had no certbot-dns-digitalocean plugin available.
After a quick search online I found that DNS Plugins are not installed by default with certbot. I needed to install certbox-dns-digitalocean plugin using PIP
Afterward, I was able to generate a certificate without many issues:
Applying SSL certificate to local HTTPS server I was able to get HTTPS valid response from the internal IP address using a domain name
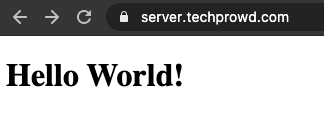
Now that I know that I can generate & use an SSL certificate for internal IP address just by using a domain name. Now I can try to migrate this knowledge to integrate this to microk8s local setup.
Integrating Let's Encrypt with DNS challenge into microk8s setup using cert-manager
I am not going to describe microk8s Kubernetes setup as it is pretty straightforward compared to the plain Kubernetes setup.
The first step is to install cert-manager I will be using Helm to install it.
Now let's configure Certificate Issuer. I will be using the configuration for DigitalOcean but it should be pretty easy to follow instructions from documentation.
First, we need DigitalOcean API token Base64 encoded to be saved in secrets
You can encode token to base64 using echo -n "Token" | base64
Now we need to configure Certificate Issuer. (I had to change kind from Issuer to ClusterIssuer because of namespace issues)
Now that we configured everything we should use the SSL certificate somewhere for this article I will configure microk8s ingress to allow access to kubernetes-dashboard via https://server.techprowd.com/dashboard
Now after applying the resources we can check if our certificate resource was created and check if our Let's Encrypt Certificate was created too
Now that everything created we should be able to access https://server.techprowd.com/dashboard
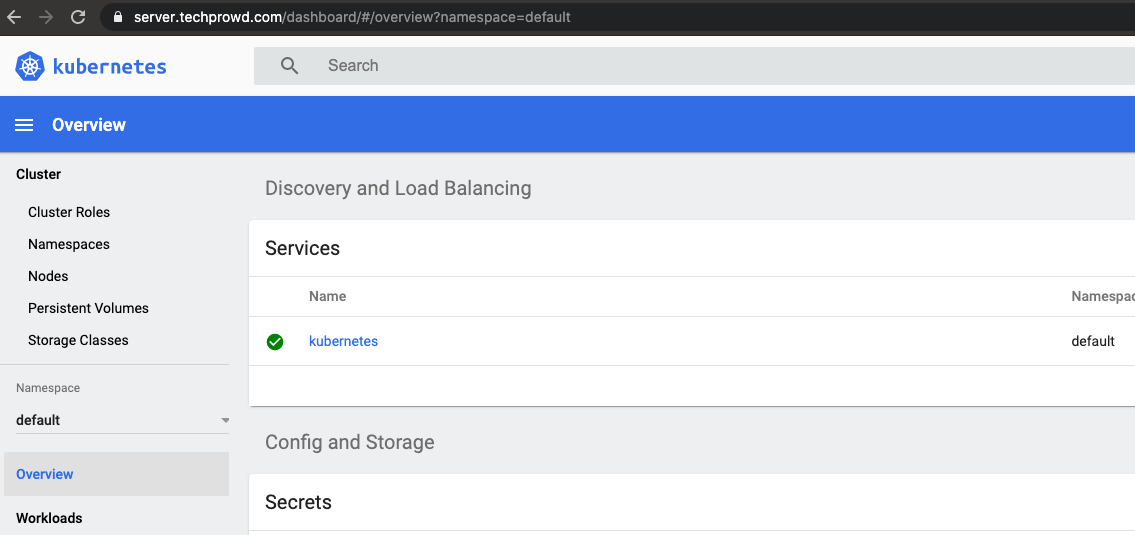
If I understood correctly the Certificate will be automatically renewed when expiration time comes up.
So that's all for this article. I hope this helped other people who had similar ideas like me when started working with Kubernetes.
P.S. I am not a professional Kubernetes engineer and everything mentioned in this article is just my assumptions and trying out practices in the local environment.
